Webhards is a platform used to distribute malware, and it is mainly used by attackers that mainly target Korean users. The ASEC analysis team has been monitoring malware types distributed through webhards and has uploaded multiple blog posts about them in the past. Various types of malware are used recently such as UdpRat or DDoS IRC Bot developed with GoLang, but njRAT had been used in multiple attacks in the past.
- njRAT Malware Distributed via Major Korean Webhard
- 파일 공유 사이트(성인물) 통해 유포 중인 Korat 백도어
- njRAT Being Distributed through Webhards and Torrents
The ASEC analysis team has recently found njRAT being distributed through webhards. As shown in the figure below, malware disguised as an adult game was uploaded in a certain webhard.
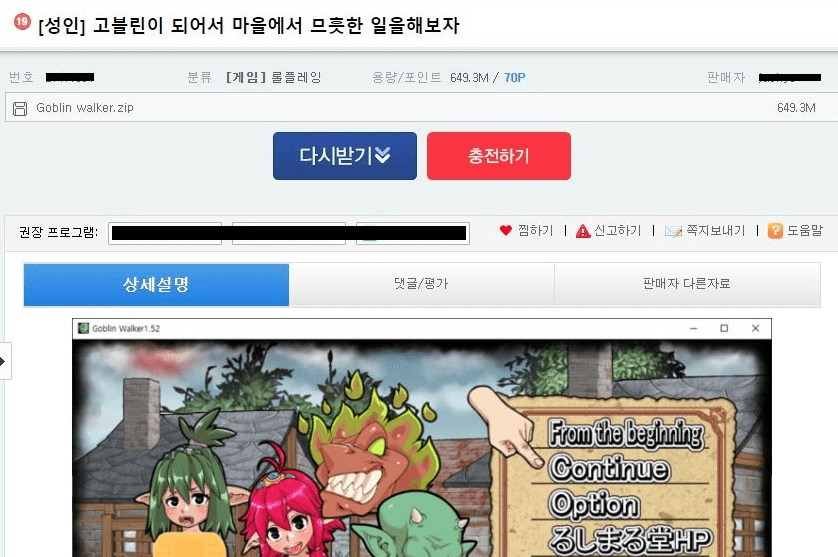
Users who download the game would probably decompress the file ‘Goblin walker.zip’ and run the executable that has the game icon image within the file. The executable is a dropper malware that contains the original game file and njRAT. When it is run, it drops and runs the game executable and njRAT in the path %APPDATA% (see figure below).

As dropper malware runs both njRAT and the game at the same time, users will find that the game is run normally.

Dropper is developed with .NET, and it has the loader (fluxfog.dat), original game executable (barsgiant.dat), and njRAT (gemsintoxicant.dat) in encoded forms (see figure below).

The dropper first decodes the loader (fluxfog.dat) and loads it in the memory. The loader’s function is to write the original game executable “barsgiant.dat” and njRAT “gemsintoxicant.dat” in %APPDATA% path and execute each file.

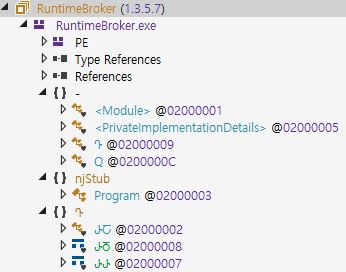
njRAT is created as a file named RuntimeBroker.exe in %APPDATA% path and then executed. Its code is obfuscated, but structurally, it is easily recognizable as njRAT (see figure below).
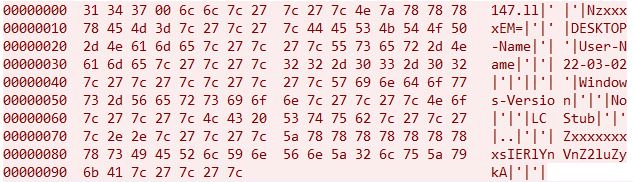
njRAT is a RAT malware that can perform various malicious activities after receiving commands from the attacker. It provides various features such as file downloading, command execution, keylogging, and user account credentials extortion. The following figure shows the C&C URL and port number that is shown when the internal settings data is decrypted.

Since njRAT used in the attack has “|’|’|” as separators, it is likely that the attacker downloaded the publicly released njRAT builder and used it without major modifications.
As shown in the examples above, the malware is being distributed actively via file sharing websites such as Korean webhards. As such, caution is advised when running executables downloaded from a file-sharing website. It is recommended for the users to download products from the official websites of developers.
[File Detection]
– Malware/Win.Generic.C4918227 (2022.01.18.00)
– Dropper/Win.NJRat.R475688 (2022.03.02.00)
[IOC]
File
– Dropper: 74cb8c2a5badf88b7407cc187b1b0adf
– njRAT: 228a44d74c4be3555a55e432967adcf6
C&C
– lllopq.ddns[.]net:3270
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
Categories:Malware Information
[…] File-sharing sites are the main platform alongside torrents used by threat actors to distribute malware to Korean users. Registered users upload media files such as movies and TV series, as well as programs such as games and utilities, and also adult content. Other users can pay a set fee and download the uploaded files. The ASEC analysis team is monitoring malware being distributed via file-sharing sites and has shared information over multiple blog posts in the past.[2] [3] [4] […]